Currently at Innoculator, the team are deep in testing our platform before making it generally available to the public (Not long now…). But whilst we are doing this, I thought I would share how easy (and groundbreaking) Innoculator makes it to virtually patch something as common as Log4Shell. I know we talk about this vulnerability a lot on this blog post, but it really is a pernicious one that keeps helping attackers whilst defenders have been struggling with this issue since it was discovered.
So with that in mind, I thought I would show you how easy it is solve it using Innoculator. The below steps are assuming you have your system setup (as in Innoculator is installed, both the HQ and the Inspectors) , and you have configured your workloads accordingly.
It then becomes a few simple steps to add protection:
Step 1 : Put the vulnerability into Innoculator HQ – Simple step, just put he CVE into the Vulnerabilities: CVE-2021-44228.
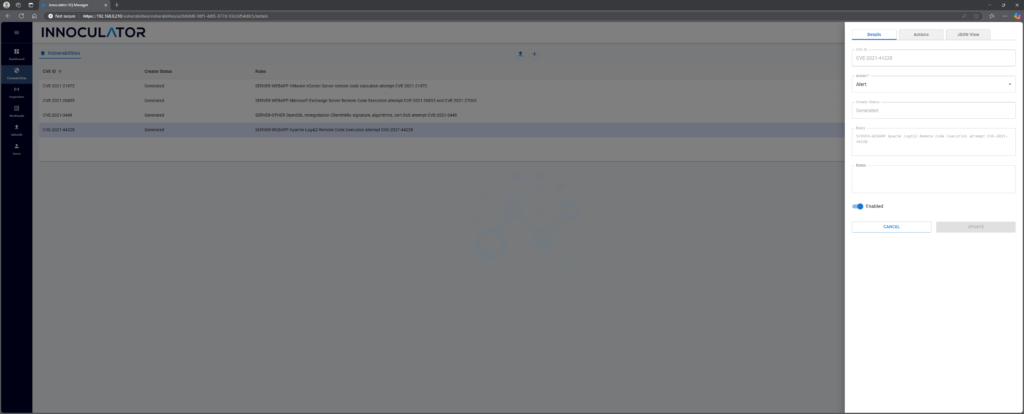
This will then request the signature form Innoculator Creator (our cloud based AI).
Step 2 :Select the Workload with the vulnerability
(Note this is how you would do it for an individual workload, we have a bulk method as well!)
So now navigate to your workloads you have in Innoculator HQ and select the one you want to add this virtual patch to:
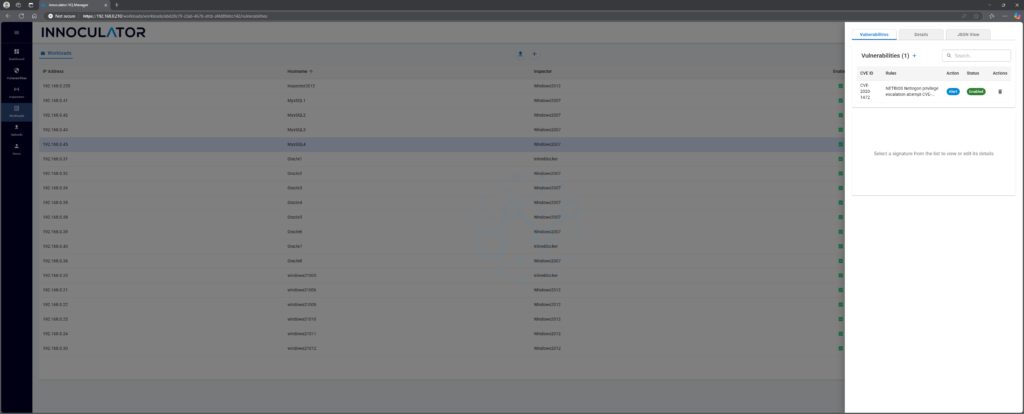
Step 3: Click “+” button to add a Signature to this workload and put CVE number in:
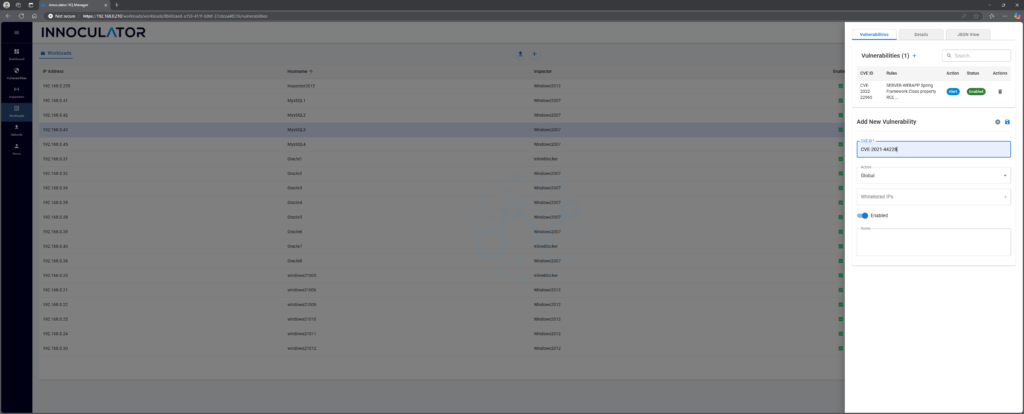
Step 4: Don’t forget to click Save!
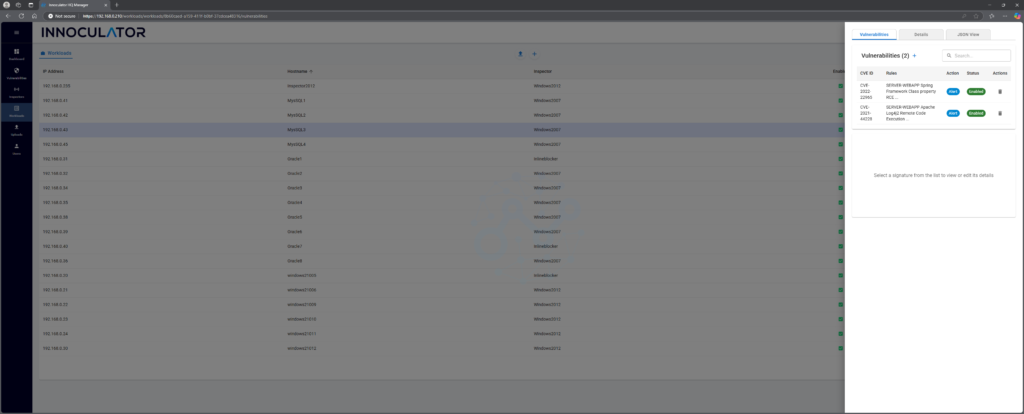
And there you have it, Log4Shell protection is in place. But before we pop the champagne corks, there are a few options you might want to consider.
Firstly, by default Innoculator is in Alert mode. So, if someone tries to exploit this, you will be alerted it, but that is all. You may want to change this to Drop, so any attempts to call this will be dropped (and you will still be alerted). As long as you have the Innoculator Inspector instance set to In-line mode, you can do this easily enough by clicking on the rule in the workload and selecting Drop from the Actions drops down menu.
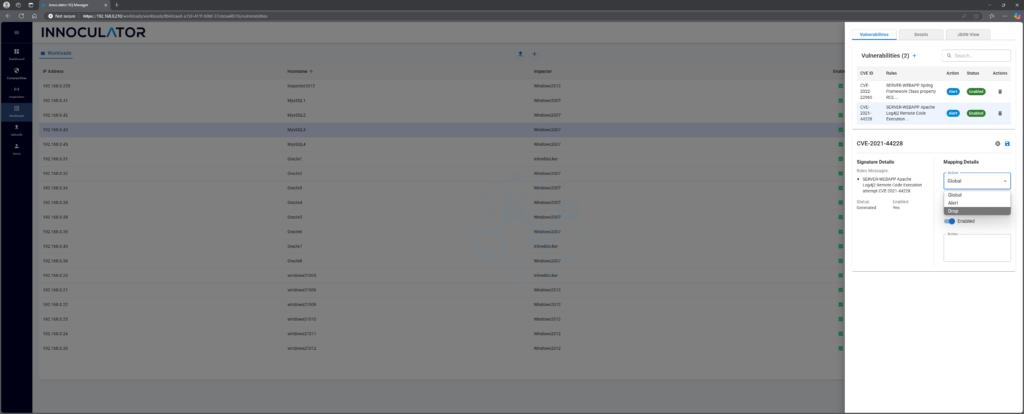
Now this raises a conundrum for some people. You may have a legitimate reason for an application to need to access workload’s log4Shell function. Don’t worry, we have you covered. With Innoculator, you can whitelist sending traffic from specific IP addresses. So if you need to do this, just click on the edit button again and add the IP address:
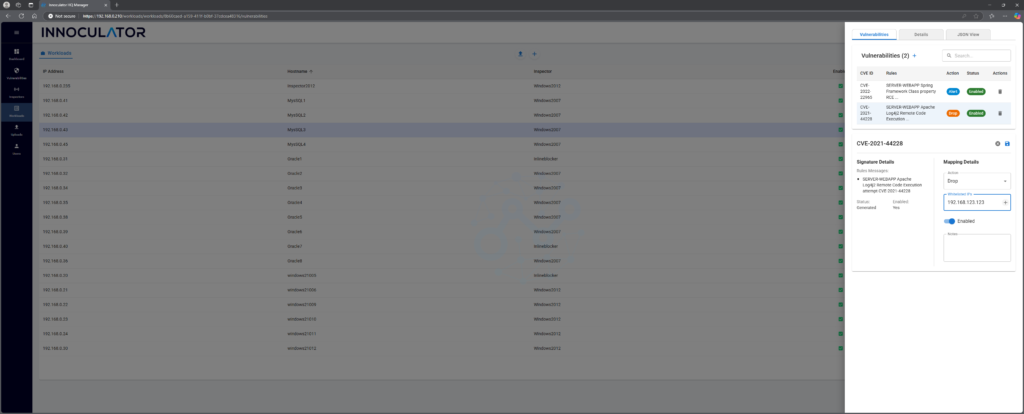
And you are done!


